Connecting your business. A cost-effective alternative to MPLS
In the IT sector, as in life in general, we tend to use what works. If hardware, software, or a particular process is ‘what all Read More …
In the IT sector, as in life in general, we tend to use what works. If hardware, software, or a particular process is ‘what all Read More …
Does your team already have the skills required to get the job done? That, in a nutshell, is the first question you ask before you Read More …

Juniper Networks yesterday released a security advisory of a serious vulnerability in JunOS. It relates to a an information leak in J-Web, the web based Read More …

Devops (development and operations) is a type of agile relationship between Software Development and IT Operations supporting it Most organisations producing software have, by now, Read More …

Amazon Web Services has evolved beyond being just a cloud platform for websites and web applications. A broad range of services which AWS provides today can be put Read More …

Understanding where the firewall sits in the topology is key, as over time, new networks are added, removed or duplicated for any number of reasons. Read More …
An important part of any security compliance audit is the ability to show that a firewall’s production configuration is compliant with the organization’s stated policies. Read More …
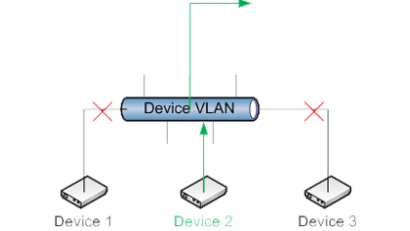
A recent article at Network World by Zeus Kerravala highlighted the design phase as the most cost effective point to apply an IofT security strategy. We couldn’t agree more. In Read More …
A common assumption when troubleshooting cloud application performance is that a network fault is the root cause. But that turns out to be the case less than 50% Read More …
Property Management Systems – Regaining control over expanding automation and control systems
Municipal Operations Systems – Building a homogeneous control and monitoring network for municipal infrastructure
Read More …