You don’t need to spend billions to get security like Google
Companies are more cognizant of the need for security for their business and customer data in 2016. Somewhat counter-intuitively, many companies seem more complacent than Read More …
Companies are more cognizant of the need for security for their business and customer data in 2016. Somewhat counter-intuitively, many companies seem more complacent than Read More …

Juniper Networks yesterday released a security advisory of a serious vulnerability in JunOS. It relates to a an information leak in J-Web, the web based Read More …

Understanding where the firewall sits in the topology is key, as over time, new networks are added, removed or duplicated for any number of reasons. Read More …
An important part of any security compliance audit is the ability to show that a firewall’s production configuration is compliant with the organization’s stated policies. Read More …
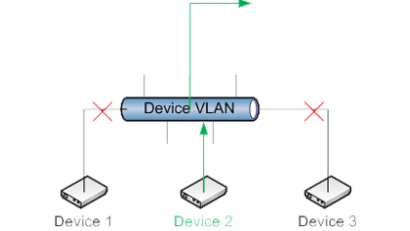
A recent article at Network World by Zeus Kerravala highlighted the design phase as the most cost effective point to apply an IofT security strategy. We couldn’t agree more. In Read More …